This minor update strengthens AD risk assessments with a new check for spotting dMSA-related risks in Windows Server 2025, improved detection of certificate service misconfiguration (ESC1), and greater deployment and authentication reliability.
What’s Changed in Netwrix PingCastle 3.4
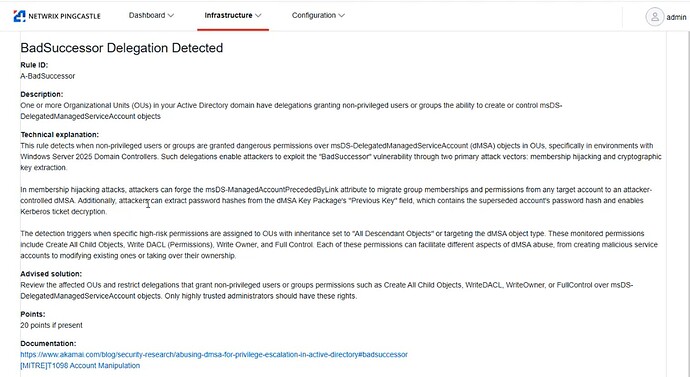
New Check: BADSUCCESSOR Delegation Detected
Flags OUs where risky permissions (e.g., CreateChild, WriteDACL) granted to non-privileged users could enable dMSA abuse and domain compromise in Windows Server 2025 environments.
Based on research from Akamai, for more details, see the community post below.
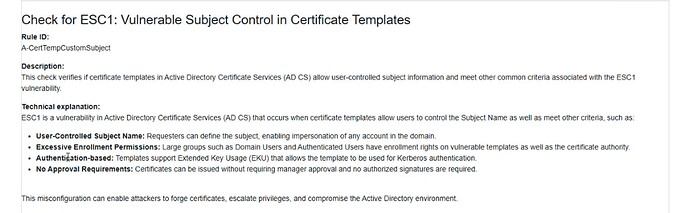
Improved ESC1 Risk Detection and Remediation
The ESC1 check — used to detect misconfigurations in Active Directory Certificate Services that could enable privilege escalation — has been enhanced to improve detection accuracy and streamline remediation
- Privileged Mode support
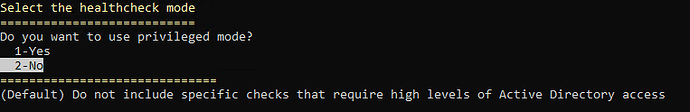
The ESC1 check now supports Privileged Mode—an optional feature that enhances scan depth when administrative access is available. By retrieving Certificate Authority ACLs, PingCastle can more precisely detect risky configurations, such as low-privilege users with certificate enrollment rights, and reduce false positives.
Expand to see how to activate Privilege Mode
Via Interactive Mode
When running an interactive HealthCheck scan, customers will be > presented with a new option
Via Command Line
To run Privileged scans via the command line, use the
--Privilegedoption.Example:
Example:.\PingCastle.exe --healthcheck --Privileged --server domain.localPrivilege Details
The table below details all specific access needs of Privileged Mode and > what each rule is for.
RuleId Access Needed Notes A-CertTempCustomSubject Remote Registry on discovered Certificate Authorities False positive mitigation for when low privileged groups have been removed from the CA Servers enrollment permissions.
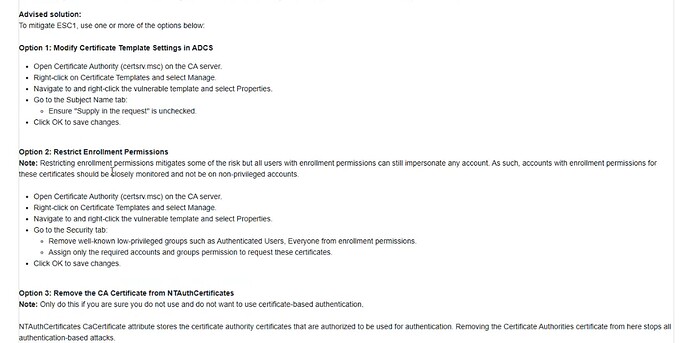
- Enhanced Remediation Guidance
Technical details and remediation steps have been updated to help security teams take swift, informed action when ESC1 risks are detected.
Improved External Authentication Handling
Following the improvements introduced in version 3.3.0.11, external authentication has been further refined for increased reliability and predictability:
- Better handling of
http://localhostduring Entra ID authentication flows - Additional stability improvements for OAuth-based authentication scenarios
Netwrix Branding
The Netwrix PingCastle web interface and HTML reports now reflect Netwrix branding, delivering a consistent look and feel across all Netwrix solutions.
Windows Server 2025 Support
PingCastle now supports Windows Server 2025 environments.
Breaking Change: SQL Encrypt Now Defaults to True
To align with changes to ADO.NET and prevent common SQL connectivity issues, the MSI installer now includes two secure default options:
TrustServerCertificate = TrueEncrypt = True
The breaking change is that Encrypt is now set to True by default. This may cause connection issues in environments where SQL Server encryption is not configured. To resolve this, you can either enable SQL encryption on the server or set TrustServerCertificate = True in the connection string.
Expand to view the process to manually update the connection string
Process
- Login to your PingCastle Application Server.
- Navigate to your PingCastle installation directory, typically
C:\PingCastleEnterpriseorC:\PingCastlePro.- Open the
appsettings.production.jsonfile in a text editor such as Notepad.- Add the following to the
ConnectionStrings → DefaultConnectionproperty:
Encrypt=True;TrustServerCertificate=True;- Save the file.
Example:
"ConnectionStrings": { "DefaultConnection": "Server=.\\SQLExpress;Database=PingCastleEnterprise;Trusted_Connection=True;MultipleActiveResultSets=True;Encrypt=True;TrustServerCertificate=True;" }New Installations
Customers installing a new PingCastle deployment will have the option to configure
EncryptandTrustServerCertificatesettings as needed during installation on the Connection String settings page.
Bug Fixes and Miscellaneous Updates
| Id | Title | Type | Case |
|---|---|---|---|
| 391119 | [Enterprise] The order of the buttons for Entities organization | Bug | |
| 392262 | Add new Functional Levels | Bug | |
| 393263 | Found legacy risk code. Convert or remove from repo | Bug | |
| 391011 | After the new exe file is copied with autoupgrade, the client will receive a non-working product | Bug | |
| 391976 | [Enterprise] push from the GlobalRiskScore page to the page with domains filtered by score does not work | Bug | |
| 391576 | [Pro/Enterprise] we need to revert or change the HTTPS Redirection change that was implemented with the HSTS changes… | Bug | |
| 391004 | [hilbert_map][Enterprise] The legend is not located near the mouse cursor, but somewhere to the side | Bug | |
| 359448 | Scanner: SMB detection of 3.1.1 does not work | Bug | |
| 391288 | [Enterprise] View details on Agent differents versions card do not redirect anywhere | Bug | |
| 391270 | [Pro] The Update page is missing / we should remove this option from configuration | Bug | |
| 390789 | [Enterprise] The product version is not added into the MSI | Bug | |
| 390673 | Entity “All Data” is missing in “Dashboard => All Domains” | Escalation | 447492 |
| 390790 | [Enterprise] the pingcastle exe is not part of the enterprise msi setup anymore | Bug | |
| 388602 | Claims Permissions on Entities not showing the Dashboard? | Bug | |
| 387290 | False Positives in S-Inactive | Escalation | 445547 |
| 389313 | Fix extensions in S-FolderOptions | Bug | |
| 387441 | POST /api/AnomalyException Issue | Bug | |
| 387281 | Entra Scans: Application Missmatch | Bug | |
| 387329 | Configuring ‘Number of Days’ on Settings causes crash | Bug | |
| 386600 | [Enterprise] PingCastleEnterprise.Controllers.AccountController.Login / An exception was thrown while deserializing the token. | Bug | |
| 382141 | [Enterprise] When loading a report, n identical warning messages are written to the Application log | Bug | |
| 386246 | [OData] Parsing Select and Expand failed: Term ‘@odata.type’ is not valid in a $select or $expand expression. | Bug | |
| 385980 | Installer: Destination Email | Bug | |
| 378558 | [Object reference not set to an instance of an object.] None of the buttons for generating data for the demo on POK work | Bug | |
| 380747 | [AzureAD checks] The amount of properties we request has changed and decreased. | Bug | |
| 361560 | [Str] The version of the product that we currently build is lower than the one that has already been released to the public | Bug | |
| 376492 | [Enterprise] The AutoUpdater should be hidden from the product | Bug | |
| 378389 | [Report Import] Manual report loading is limited to 25 MB / hardcoded value in import.js file | Bug | |
| 381819 | [Standard] The risk model section is clickable and allows you to collapse this table / based on the formatting it shouldn’t be like this | Bug | |
| 384119 | [Enterprise] Email field is not mandatory and is not checked for completeness user creation /edit | Bug | |
| 380181 | Error on Duplicate Email | Escalation | 440217 |
| 378617 | [Enterprise] Remove “New” tags from non-new functionality. | Bug | |
| 381947 | Umlaute are replaced with a “?” | Escalation | 441483 |
| 380204 | [Standard] launched from [Enterprise] folder - Could not load assembly when trying to collect AzureAD | Bug | |
| 380699 | [Checks] Typo in LDAP query for P-RODCKrbtgtOrphan | Bug | |
| 380169 | [Pro] AzureAD Config in installer results in non-working product. | Bug | |
| 375107 | [Pro/Enterprise] Enhance installer checks for IIS and ASP.NET | Bug | |
| 377326 | Deprecation of ProvisioningAPI | Feature | |
| 374720 | Implement filtering of ASR Rule based on presence of Exchange | Escalation | 435268 |
| 374636 | PingCastle not collecting Azure data | Escalation | 435212 |
| 377741 | Add AdminSDHolder to critical infrastructure list | User Story | |
| 364407 | Update the Windows SunBurst OS List | User Story | |
| 376493 | The Sunburn OS selector is unfull of version | Bug | |
| 376494 | The windows sunburn is incomplete with version | Bug | |
| 374321 | Client license is not automatically replaced at start | Escalation | 434838 |
| 374942 | [Pro/Enterprise] After installation, the customer will receive a non-working product. | Bug | |
| 375105 | [Pro] EF Core Version Mismatch / Leads to a non-working product | Bug | |
| 374567 | Issue with LAPS Reporting in Pie Charts and Table | Escalation | 435091 |
| 368888 | Permissions on Entities | Escalation | 430048 |
| 365582 | PwdLastSet is missing in some of the outputs | Bug | |
| 392269 | Fix Typo | Bug | |
| 392270 | Fix Typo | Bug |
Plan your upgrade
Netwrix PingCastle 3.2 will reach its end of support life on January 10, 2026. To learn more, please read the Netwrix End-of-Support Policy.
Need help with this update?
There are many different ways to get help with our products!
| Situation | Action |
|---|---|
| If you feel the product is broken and not working as intended… | Contact Support |
| If you have a question you’d like to ask other experts… | Create a discussion in the community: PingCastle > Discussions & Questions |
| If you have a feature request… | Let our product team know directly: PingCastle > Ideas |
| If you have something cool to show… | Show everyone what you built: PingCastle > Show & Tell |
What are your thoughts?
We are always happy to hear from our users on what you like, and what you hope to see in the future. Please, share your thoughts below!