Hi there everyone!
Just wanted to let you all know about some new research that came out in the AD Security space just yesterday.
There is a new attack vector in Active Directory where an attacker could abuse basic “Create all child objects” or specifically the create dMSA permission to create and use a Delegated Managed Service Account (dMSA) to compromise the secrets (password hashes) of any account in the domain.
This research was built on some previous research I did on how to extract dMSA password hashes from Active Directory using the new DMSA-Key-Package which you can see the basics of in this Rubeus PR I created in November last year (#194) and then Yuval’s new PR (#204) to extend the functionality for the new research.
You can find Yuval Gordan’s great research on this new attack technique over at the Akamai Security Research blog
https://www.akamai.com/blog/security-research/abusing-dmsa-for-privilege-escalation-in-active-directory
What should I do?
We have released a new pre-release build of PingCastle specifically with some changes to help customers detect potentially risky delegations on their OUs. You can find the pre-release build in GitHub releases here.
You can then just run this as you would normally and check out the Anomaly section for “BadSuccessor Delegation Detected” to see if you are affected.
If you have no Windows Server 2025 Domain Controllers then this will not show up but you can use the “All Delegations” table and look for the following permissions with or withouth the (msDS-DelegatedManagedServiceAccounts) next to it to find instances of the risky permissions:
- CreateChild (All Objects)
- WriteDACL (All Objects)
- GenericAll (All Objects)
- WriteOwner (All Objects)
- CreateChild (msDS-DelegatedManagedServiceAccounts)
- WriteDACL (msDS-DelegatedManagedServiceAccounts)
- GenericAll (msDS-DelegatedManagedServiceAccounts)
- WriteOwner (msDS-DelegatedManagedServiceAccounts)
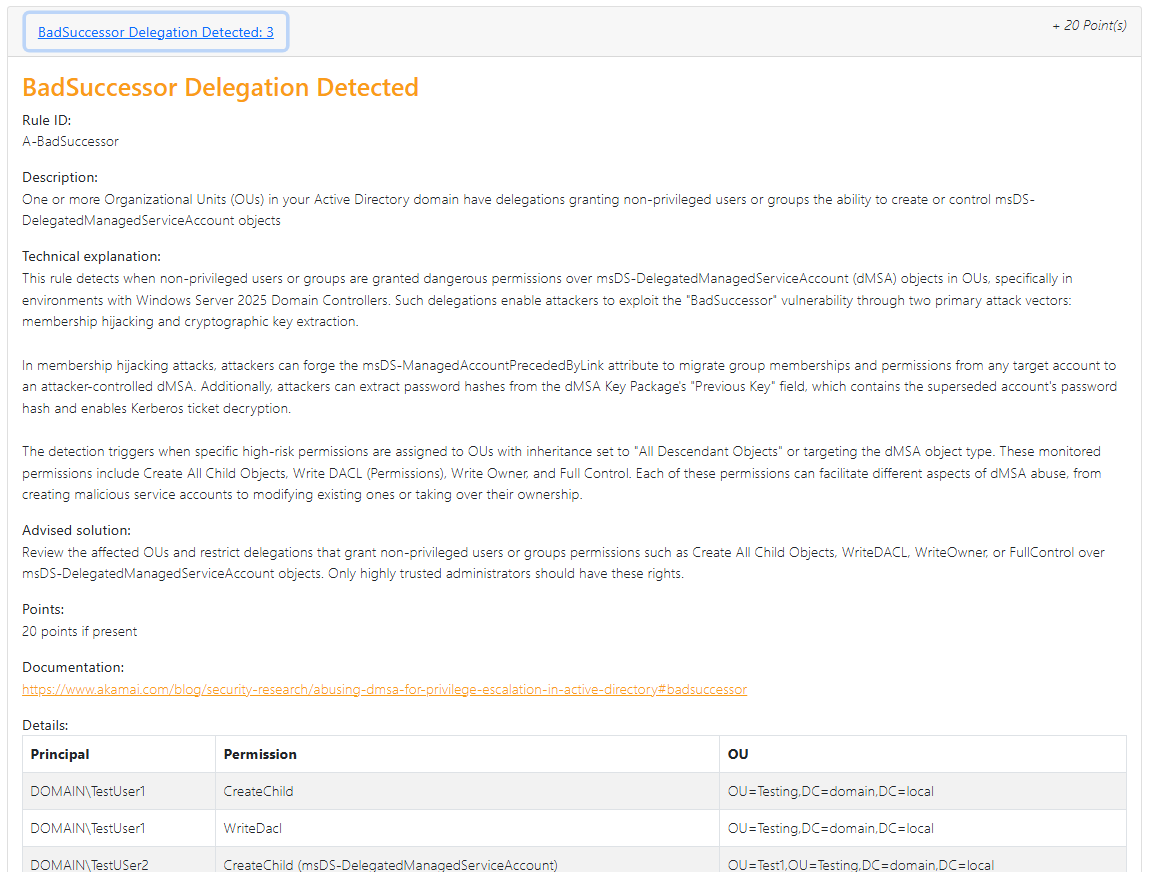
Here is an example of what the risk looks like in the beta build
The code for the beta build can be found at in the BadSuccessor branch on GitHub: GitHub - netwrix/pingcastle at BadSuccessor
Hope this helps! ![]()
Edit: updated the permissions that can be searched in the delegations table as we split these out further to reduce some false positives.