Netwrix is pleased to announce the general availability of Netwrix Privilege Secure July ‘25 Release (v25.08.04003) .
Heads Up: Netwrix Privilege Secure Version Numbering Has Changed!
We’re excited to announce a new release—now using our brand new version numbering! Instead of 4.x, you’ll see versions like v25.05 or v25.06.
Curious why? Check out our version numbering change announcement
Netwrix Privilege Secure July ‘25 Release (v25.08.04003) is Now Live!
The documentation for Privilege Secure July ‘25 release (v25.08.04003) is in progress and will be available at a later date. Please see the following ‘What’s New’ section for new features, bug fix lists, and other information about this release.
What’s New
Features
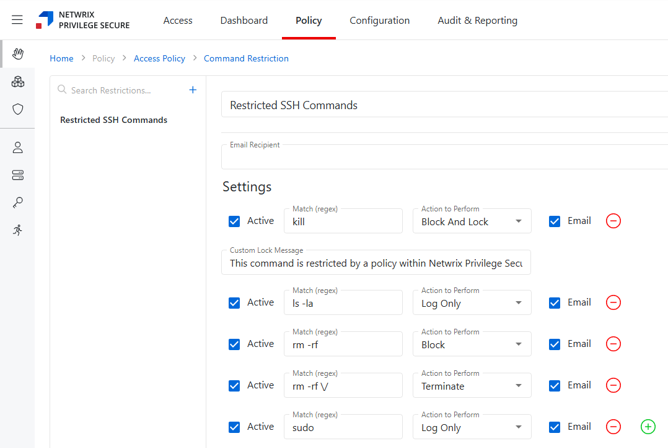
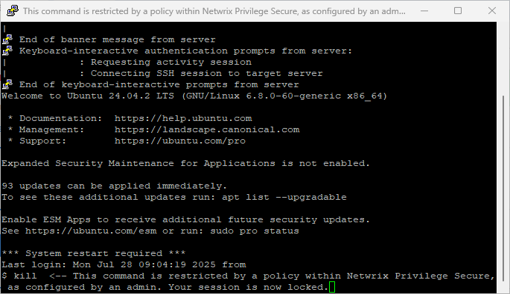
Command Restrictions for SSH
Specific commands can be restricted during SSH sessions using regular expressions. The system evaluates commands in order from top to bottom, applying the first matching rule. Available actions include logging the command, blocking it, locking the session, or terminating the session. Custom lock messages can be configured per command when using the lock action. Email notifications can be sent to Privilege Secure administrators whenever a restricted command is triggered. Restrictions are configured in the new Command Restrictions section within the Policy tab.
Expire Idle Users
Users who have not logged in to Privilege Secure for a configurable number of days can now be automatically disabled. Disabled users do not consume a license credit. Admins and Application users are exempt from this policy. The idle timeout can be set to a specific number of days or turned off entirely. This setting is available in Global Settings under the Configuration tab and is disabled by default.
Bring your own vault® (BYOV) for Password Secure
Netwrix Privilege Secure now integrates with Netwrix Password Secure to enable centralized, secure management of privileged credentials. This allows organizations to perform actions as specific users using credentials stored and managed in Password Secure, without exposing or manually handling those credentials. The integration streamlines privileged access workflows across both platforms, enhancing security and operational efficiency.
Other Changes
- Added tool tips for Dashboard tiles to show exact numbers on hover
- Added “Run-ADSyncForDomainAndObject” as a new action step
Bug Fixes and Miscellaneous Updates
This list includes the most significant fixes in this release; numerous minor bugs have also been addressed.
| ID | Decription |
|---|---|
| 373712 | Browser Extension: Resolved “Clear Website Data Before Start” not targeting cached admin.microsoft.com data |
| 381101 | Resolved an issue preventing Task Automation sessions from ending |
| 384101 | Stopped High Availability configuration tool from generating numerous pg_hba.conf.old files |
| 391963 | Resolved an issue that could cause discrepancies in SIEM event times |
| 391964 | Prevented incorrect password changes in certain multi-activity scenarios |
| 392764 | Prevented Content Security Policy from breaking the Secure Remote Access portal UI |
| 394009 | Non-Default Connection Profiles are now updated to record keystrokes if session recording was already enabled when upgrading |
| 394452 | Resolved situation that could prevent Secure Remote Access portal sessions from connecting |
| 394483 | Prevented host scan from marking computers as “WinRM Disabled” if it cannot find a host online during subsequent host scans |
| 395827 | Resolved Cisco OS detection for Linux causing an issue with certain Cisco devices |
| 396697 | Resolved copy/paste not always functioning during Secure Remote Access sessions |
Plan your upgrade
Netwrix Privilege Secure 4.1 will reach its end of support life on November 30, 2025. To learn more, please read the Netwrix End-of-Support Policy.
Need help with this update?
There are many different ways to get help with our products!
| Situation | Action |
|---|---|
| If you feel the product is broken and not working as intended… | Contact Support |
| If you have a question you’d like to ask other experts… | Create a discussion in the community: Privilege Secure > Discussions & Questions |
| If you have a feature request… | Let our product team know directly: Privilege Secure > Ideas |
| If you have something cool to show… | Show everyone what you built: Privilege Secure > Show & Tell |
What are your thoughts?
We are always happy to hear from our users on what you like, and what you hope to see in the future. Please, share your thoughts below!