The Challenge: Manual Investigation
Netwrix Auditor is excellent at capturing the critical evidence you need. It provides detailed Activity Records, giving you visibility into every important action in your environment.
During an investigation, all the individual clues are right there in the records. But they may look something like this:
You have all the right pieces of the puzzle — an AD account was created, a file was accessed in Azure, etc.
But it’s still your job to piece that puzzle together. Fast. And when everyone is looking to you for answers, it becomes a high-pressure, manual process.
The Solution: Automating the Analysis with MCP and LLMs
That’s exactly what MCP for Netwrix Auditor does. It’s a tool that connects to your Netwrix Auditor instance, uses an LLM (Claude) to analyze all the relevant Activity Records, and builds a complete story of the attack for you.
Here’s what that looks like:
It takes the high-quality evidence from Netwrix and presents it as a clear, step-by-step narrative.
How It Builds the Story
The report you saw in the video was created by MCP for Netwrix Auditor based on its analysis of the Netwrix data. It’s not just a dashboard; it’s a full investigation report.
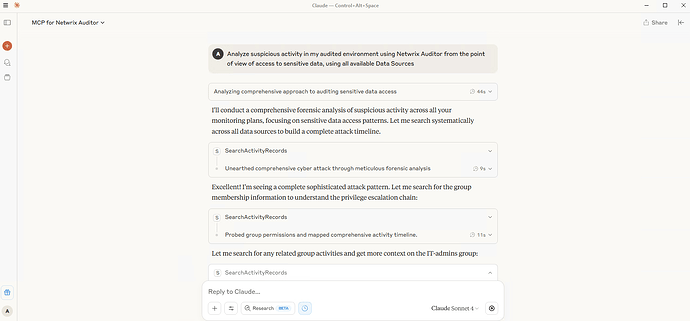
It starts with a simple question.
No complex prompts. I just asked it to find suspicious activity related to sensitive data.
The tool then uses the Netwrix API to pull the relevant records from Active Directory, Azure, the File Server, and the User Activity Records.
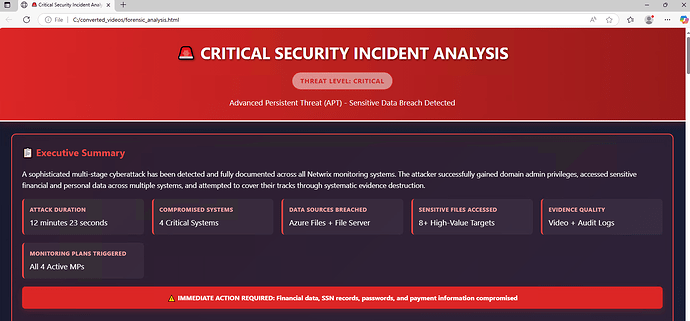
The report shows you what matters, right at the top.
You get an immediate summary of the incident—the threat level, attack type, and key metrics.
It finds how the attacker got admin rights.
The report highlights the privilege escalation path. In this case, the attacker’s user was added to a group nested inside Domain Admins.
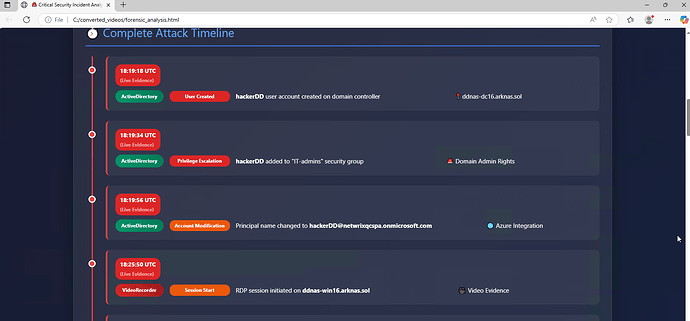
It lays out the full timeline.
This is the key. It takes events from different systems and puts them into a single, chronological story. You can follow the attacker from their first action to their last.
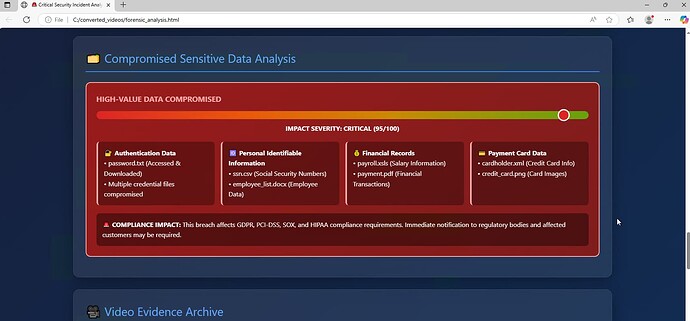
It tells you what data was affected and why it’s a problem.
The analysis flags the specific types of sensitive data accessed and points out the compliance impact (GDPR, PCI-DSS, etc.), so you know exactly what notifications are required.
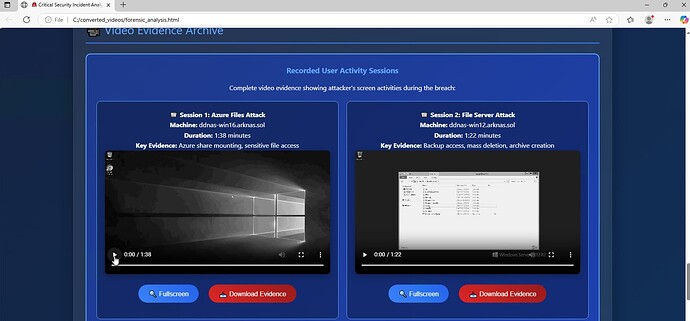
And it gives you video proof.
The best evidence you can have. The report embeds the screen recordings of the attacker’s desktop, captured by Netwrix Auditor (User Activity Video Recorder). You can watch exactly what they did.
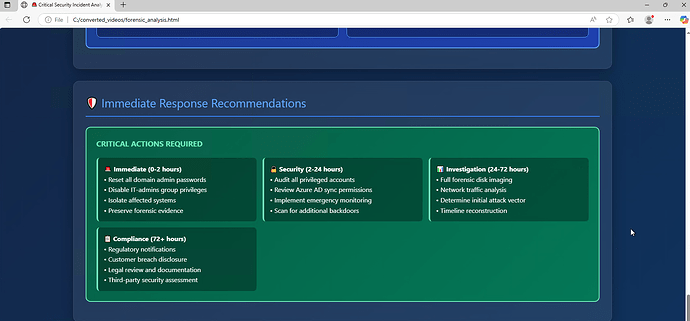
Finally, it provides an action plan.
The report ends with a simple, prioritized list of what to do next to contain the threat and recover.
A quick note: While the AI provides a solid starting point, always review and validate any AI-generated response plans with your team before taking action.
The Point
Netwrix Auditor provides the ground truth—the critical evidence you need. MCP for Netwrix Auditor builds on that foundation.
It automates the analysis part of the investigation. It connects the dots for you, so you can see the full story in minutes. This frees you up to do what you’re best at: responding to the threat and securing your environment.
Try It Yourself
This is an open-source project, and you can try it yourself.
Get it on GitHub: https://github.com/netwrix/mcp-server-auditor
We recently released a new installer that makes setup much easier. You can download it and connect it to your own Netwrix Auditor instance to see how it works with your data.