New Active Directory Threat: BadSuccessor
Have you heard of the new BadSuccessor privilege escalation technique that abuses Delegeated Managed Service Accounts (dMSAs) in Windows Server 2025? If not, be sure to check out the blog here by Yuval Gordon from Akamai.
The TLDR is essentially the following:
If a user has the ability to create an object within an OU (such as a dMSA account) they can become Domain Admin.
- Create a dMSA account in an OU that you have privileges to do so
- Grant yourself permissions to modify the dMSA account that you just created
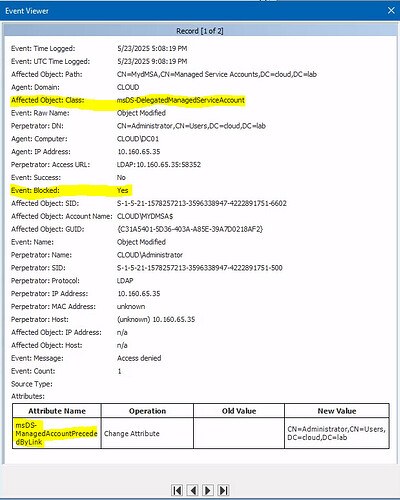
- Modify the msDS-ManagedAccountPrecededByLink attribute on the created object to a privileged account
- Leverage tools to get the hash of the defined preceded account
This is all because Microsoft is not currently validating the msDS-ManagedAccountPrecededByLink attribute value to ensure it was actually a migration of the preceded account. Learn more about this process in the blog above or Microsoft documentation on dMSAs.
Description
Here is a very simple policy that can help you monitor and/or block potential changes to the msDS-ManagedAccountPrecededByLink attribute. As always, you can add exclusions to allow certain users from performing these changes, but prevent every other user in the organization from making them.
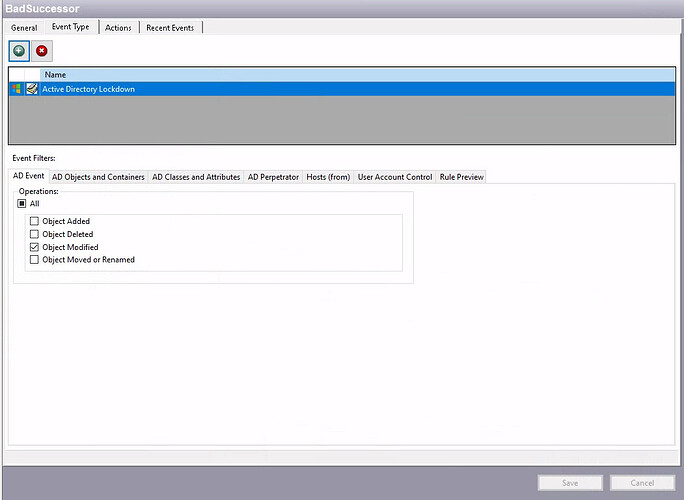
- First, create a fresh policy and either choose Active Directory Lockdown or Active Directory Changes, I’m going with lockdown in my example.
- Choose the ‘Object Modified’ AD event operation.
- Optionally, navigate to the AD Objects and Containers tab and provide an Allow list of users that can make these changes in your organization.
- Finally, go to the AD Classes and Attributes tab and select the msDS-ManagedAccountPrecededByLink attribute.
After you save the policy and enable it, Netwrix Threat Prevention will begin monitoring (or blocking!) changes to the msDS-ManagedAccountPrecededByLink attribute.