Overview
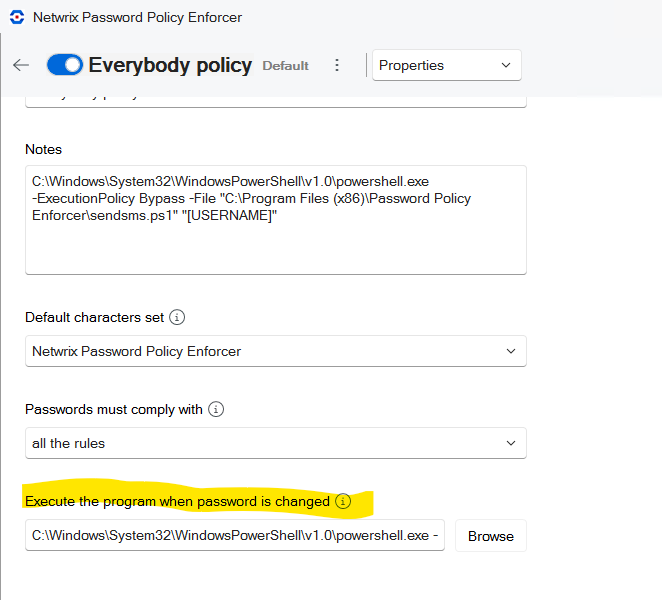
A little known but powerful feature of Netwrix Password Policy Enforcer is the ‘Execute A Program When Password is Change’ setting in the properties pane of each policy:
This feature will allow you to call a program or script when a user changes his or her password. This can be used to sync credentials, launch another process or in this case, send an SMS message to the user notifying them that their password has changed. This can help protect against unexpected password changes done by bad actors via phishing, social engineering, or lateral movement.
Netwrix Support has a great article on how to set this up for Twilio or Azure Communication Services. However, recently a customer whose DC’s do not have direct internet access asked me how to do this via a proxy. One answer is to use Powershell with WinRM and execute the Powershell on an internet connected machine.
Although you shouldn’t hardcode credentials into a script, I’ve left it this way because many organizations, have different options for how to manage credentials. You can use Windows Credential Manager or your own vault (or Netwrix Privilege Secure).
Here’s a simple outline to get you started:
Pre-Requisites
1. Twilio Account
- Sign up at Twilio.
- Buy an SMS-enabled phone number.
- Obtain your Account SID and Auth Token from the Twilio Console.
2. Active Directory / Permissions
- Script typically runs as a service account with permissions to:
- Query user accounts (
Get-ADUser). - Log in remotely (for
Invoke-Command).
- Query user accounts (
- On the target server (e.g., the jump server/bridge):
- That user must be a member of the appropriate groups (often
Remote Management Users). - The server must allow remote PowerShell (
Enable-PSRemoting), and specifically CredSSP Authentication.
- That user must be a member of the appropriate groups (often
- The controlling server (e.g., domain controller) must be allowed to connect to the bridge/server using these credentials.
- Add YOURDOMAIN\YourServiceAccount to the Domain Policy in Group Policy - Computer Configuration → Policies → Windows Settings → Security Settings → Local Policies → User Rights Assignment → “Access the computer from the Network”
3. Network Requirements
- The “bridge” server MUST have outbound Internet access (port 443) to reach the Twilio API.
- Ensure firewalls permit this on the required host.
4. PowerShell Modules
ActiveDirectorymodule installed on the bridge (forGet-ADUser).- PowerShell 5.1+ recommended.
Deployment Steps
- Service Account Setup
- Create a dedicated, low-privilege domain account (e.g.,
DOMAIN\YourSmsService) with just enough rights for your scenario.
- Test Connectivity to Bridge Server
- On the controlling host, verify you can use PowerShell Remoting:
Test-WsMan -ComputerName YourBridgeServer
- Configure CredSSP Authentication if necessary.
- Example Script
param (
[string]$User
)
$username = 'DOMAIN\YourSmsService'
$password = 'ACCOUNT_PASSWORD' #use credential manager or vault to manage this
$secpass = ConvertTo-SecureString $password -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential ($username,$secpass)
Invoke-Command -ComputerName YourBridgeServer -Authentication CredSSP -Credential $cred -ScriptBlock {
param (
[string]$Username
)
# Fetch the user’s details from AD
$User = Get-ADUser -Filter "SamAccountName -eq '$Username'" -Properties MobilePhone
$Phone = "+1234567890" # Replace or fetch dynamically: $User.MobilePhone
# Twilio credentials (set in environment vars or encrypted files in real use!)
$twilioSid = "ACXXXXXXXXXXXXXXXXXXXXX" # <-- Your Twilio SID
$twilioToken = "XXXXXXXXXXXXXXXXXXXXXXXX" # <-- Your Twilio Token
$twilioFrom = "+123XXXXXX" #<--Your Twilio Number
$url = "https://api.twilio.com/2010-04-01/Accounts/$twilioSid/Messages.json"
$body = @{
To = $Phone
From = $twilioFrom
Body = "Your account password was changed. If this wasn't you, contact IT."
}
$pair = "$twilioSid`:$twilioToken"
$encodedPair = [Convert]::ToBase64String([Text.Encoding]::ASCII.GetBytes($pair))
$headers = @{ Authorization = "Basic $encodedPair" }
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
$response = Invoke-RestMethod -Uri $url -Method Post -Headers $headers -Body $body
$response | Select sid, body
} -ArgumentList $User
- Save the script to an accessible location eg. c:\PPE.
Set Argument in PPE
- Open the policy in question in PPE and navigate to the policy properties on the top menu.
- Set the following line with the correct path into the “Execute The Program When the Password is Changed” field:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -ExecutionPolicy Bypass -File "C:\PPE\PassChangeNotification.ps1" "[USERNAME]"
- Test it by changing a password of a user in that policy.
Customize as needed
- Change the body value in the script block to reflect the message you want sent to your users. Include your company or organization name and contact details as necessary.
- Let us know how it goes and help us improve this script.